Can Download but Not Upload Putty Ftsp
PuTTY is a versatile concluding plan for Windows. Information technology is the globe'south virtually pop gratuitous SSH customer. Information technology supports SSH, telnet, and raw socket connections with skillful terminal emulation. It supports public key hallmark and Kerberos single-sign-on. Information technology also includes command-line SFTP and SCP implementations. PuTTY is most commonly used on Windows. It is too available on Linux. Download PuTTY for Windows PuTTY on Linux PuTTY on Mac There many SSH clients that are more than modern. A major shortcoming of PuTTY is that it does not have integrated file transfers in the customer itself. Instead, file transfers accept to be done via the control line. This is as well complicated for most users. Tectia SSH has had them since 2000. PuTTY too does non include an SSH server. Other SSH clients PuTTY does not come with an SSH server. Information technology can exist used with Linux OpenSSH. For Windows and IBM z/OS mainframes, nosotros recommend the Tectia SSH server. Installing PuTTY on Windows Using the terminal on Windows Setting up SSH keys on Windows with PuTTYgen Setting up SSH keys on Linux with PuTTYgen PuTTY user manual Windows client. Mac and Linux ports exist. No server included. Supports both 32-bit and 64-chip Windows. An MSI installer has been bachelor since 2016. Supports SSH client, telnet client, SFTP client (command line just), and rlogin client. Both SSH2 and SSH1 protocols are supported. Notation that use of SSH1 is not recommended for security reasons. Practically all devices back up SSH2 these days. Supports public key hallmark and Active Directory/Kerberos authentication. File transfers only using a dissever control-line programs. No integrated file transfer back up. No scripting back up, just can be used together with WinSCP. The main feature of the product is the terminal window. Information technology has good final emulation, good configurability, and proficient support for different cryptographic algorithms. SSH, telnet, and patently TCP/IP protocols are supported. The PuTTY terminal is pretty good and handles terminal emulation well. The user interface does not include an integrated file transfer client. However, command-line tools called The WinSCP and FileZilla clients can also be used for file transfers in conjunction with PuTTY. Having two software packages, switching betwixt them to practice operations, and managing profiles and logins for both is extra trouble. WinSCP can now import PuTTY profiles, but separate login is still required for each. PuTTY uses its own file format for SSH keys. The keys are stored in It is mutual for hackers and malware to collect SSH keys when penetrating an organization. This happened, for example, in the infamous Sony breach. Recently, Wikileaks obtained CIA hacking tools designed to steal SSH keys and their passphrases. Managing SSH keys properly is important. Universal SSH Fundamental Director a popular SSH key direction solution and the only i at the fourth dimension of this writing that supports PuTTY grew out of a telnet client. Information technology still supports the There is a carve up version of the software, called PuTTY also supports connecting to serial ports and raw sockets. These tin can sometimes be useful for debugging purposes and for working with some legacy devices. For case, in kernel evolution admission via a series port is even so sometimes the best style to debug a panic that causes an immediate reboot, as it provides a mode to run into the boot letters. Version 0.66 and before are known to contain security vulnerabilities. Upgrading to the latest version is recommended. Buffer overflow in SCP. This a potential stack overflow and remote code execution vulnerability. A corrupt server could execute lawmaking on the client when any file is downloaded. Information technology could also exist exploited by man-in-the-heart attacks. Integer overflow in terminal escape sequence treatment. This is a memory corruption and possible remote code execution vulnerability. It involves sending an escape sequence to the terminal. For example, a compromised switch could inject the assail into a session. Information technology tin can as well exist exploited by a decadent server to execute lawmaking on the client, or using man-in-the-middle attacks. A trojaned version has been circulating. Lack of proper key management tin can expose servers to run a risk and let attackers to spread server-to-server or jump through desktops/laptops containing SSH keys. More than information on SSH fundamental direction tin exist plant here. PuTTY is one of the oldest SSH clients for Windows. It was first released by Simon Tatham in 1998. SSH back up was added in 2000. After 19 years, the software is still a beta version. Development has been slow, only it is all the same being maintained. A recent version added back up for elliptic curve cryptography. The user interface or features take non inverse much in 15 years. A Oftentimes Asked Questions certificate (FAQ) can be plant here. Source code is available on Simon Tatham'southward home page. Installation packages tin can be downloaded deeply here. The product is open source. Several projects have branched off and build on its source code. PuttyManager is a tabbed user interface, just development appears to have stopped years ago. ExtraPuTTY is a fork that has diverse extensions, such as Lua programming language integration. MTPuTTY is a version of with a user interface that supports multiple tabs (i.e., a tab command where each tab is a terminal window). WinSCP has some level of integration for file transfer functionality. PuTTY tutorial PuTTY downloads
Alternative SSH clients
How to get an SSH server
Tutorials, how-tos, and user manual
Features
Terminal window
Transferring files
PSFTP and PSCP are provided. These can be used for file transfers. Yet, most non-technical users are not willing to employ a command line. Tectia SSH, for case, has offered fully integrated file transfer capability since 2000.Public key authentication
.ppk files. The PuTTYgen tool tin can be used for generating new keys and converting between .ppk files and other primal formats..ppk files.Telnet back up
telnet protocol. Withal, very few devices use telnet these days. Its use is not recommended for security reasons.Telnet sends all user names and passwords in the articulate. It is very piece of cake to listen to network traffic and steal user names and passwords from telnet traffic. By mid-1990s, such password sniffing attacks had become the largest security problem on the Internet. That was the very problem SSH was designed to solve. Compromised routers, switches, or ARP proofing attacks can also be used to inject arbitrary commands into telnet sessions.PuTTYtel, for countries that do non permit any use of encryption. However, SSH is now used in all countries, officially or unofficially. Nearly systems can no longer be managed without encryption. Even the most oppressive countries need to secure their systems somehow. There cannot be cybersecurity in a networked environment without encryption.Known security vulnerabilities
History and maintenance status
Where to find the source code
Extensions, branches, and integrations
Videos and screenshows
Tutorial video
Terminal window
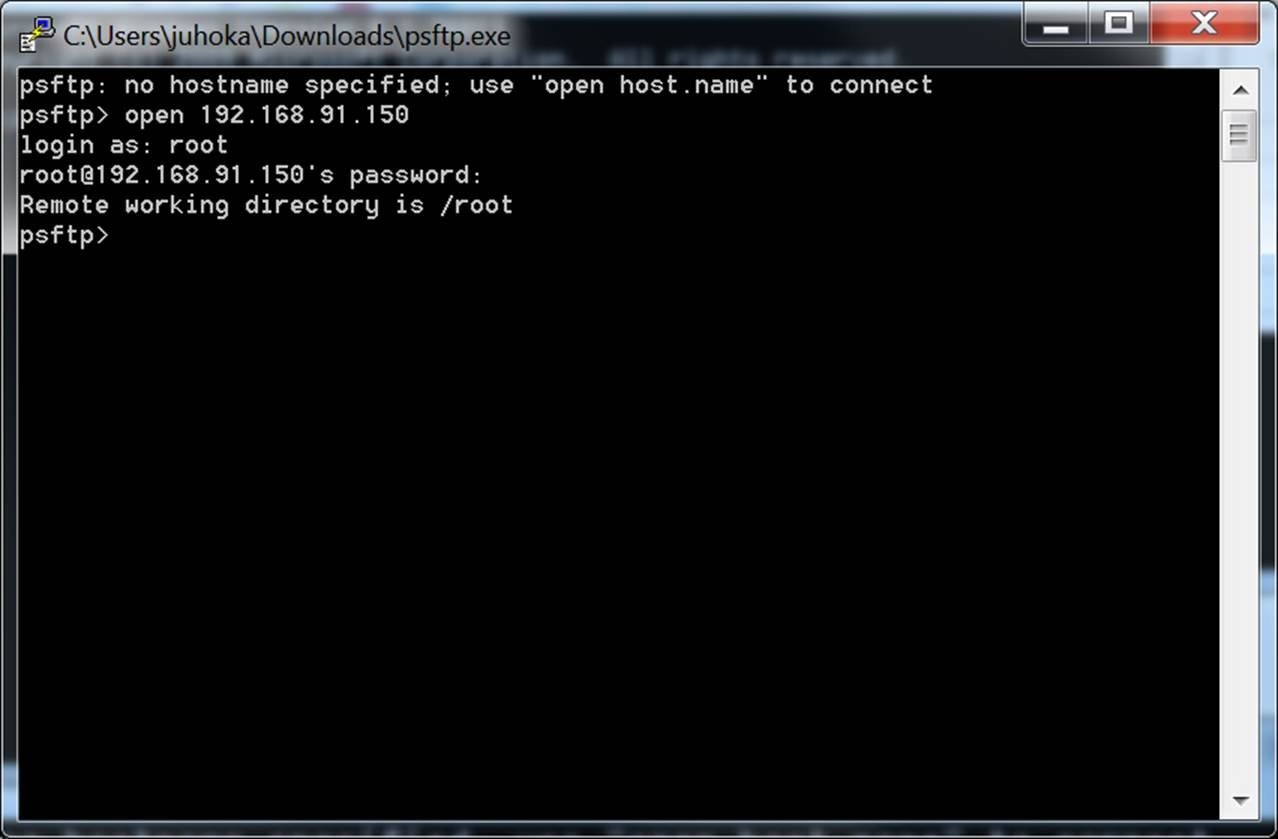
SFTP customer
Source: https://www.ssh.com/academy/ssh/putty
0 Response to "Can Download but Not Upload Putty Ftsp"
แสดงความคิดเห็น